This is a bug which is said to be very much bigger than the previous
flaw called Heartbleed, which left all the secure SSL systems
vulnerable, but this time a bug is found which able to compromise your
system and then able to run commands or execute any malicious program
onto your computer or device.
This harmful bug dubbed as ‘Shellshock’. As I said above this is a superbug, so here is, why it is called the SuperBug:
- Shellshock is a Bash bug and able to exploit any operating system.
- This Bug able to send a command to the exploited system through a code.
- The particular area, which is able to exploit the system is generally blocked, but the Bash opens all doors to the system
- Apple Mac OS X users able to run it from their terminal, others people linux operating systems also can.
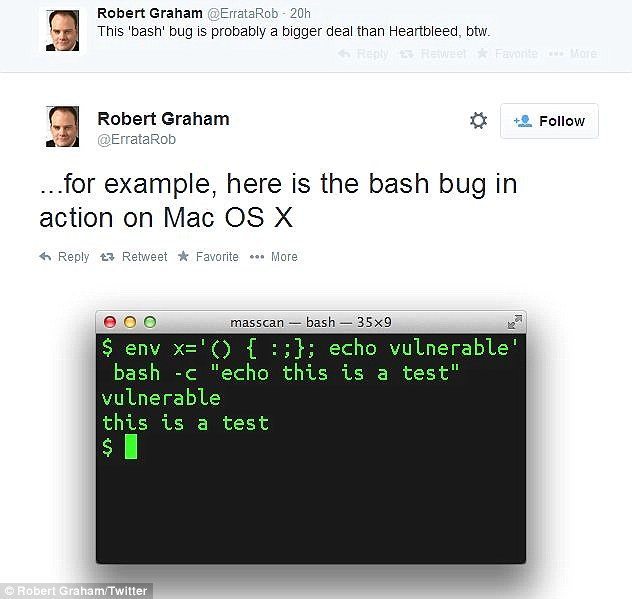
- Windows is not affected in the same way, but if a hacker exploits
malicious code through the flaw, they could gain access to any device,
in theory, including PCs.
- Working Example: As an Apache Web Sever runs bash command to process task along with the data entered in the online forms.
This flaw has been revealed by the hackers previously, and they are
using this to exploit million of users online, UK Privacy regulator has
already warned.
In simple words, The flaw is ‘Bash’ which contained in a piece of
software and that software used by the operating systems and other
website servers.
At this time, there is not any critical update or any idea found by
the security researchers to save millions of users online, and the the
UK and US governments also have issued national alerts in response to
the bug, warning that it may compromise organisations responsible for
“critical national infrastructure” such as power stations if it is not
rapidly dealt with.
Statement issued by The Information Commissioner’s Office (ICO):
The Shellshock flaw “could be allowing criminals to access personal
data held on computers or other devices”, which “should be ringing real
alarm bells” for British businesses which are legally obliged to keep
their customers’ details secure.
“The worst thing would be to think this issue sounds too complicated –
businesses need to be aware of this flaw and need to be monitoring what
they can do to address it. Ignoring the problem could leave them open
to a serious data breach and ultimately, enforcement action.”
Who found this Flaw?
This critical flaw was found on 12 September by Stephane Chazelas, a
38-year-old French software developer living in Edinburgh. This Flaw
uncovered “by chance”, he said to The Independent Today.
After finding this flaw, Chazelas reported this to Chet Ramey, a
49-year-old American programmer working at Case Western Reserve
University in Ohio, and he maintains the Bash source code.
One more important thing about the Bug is, it is in the market from
last 25 years and there is a question on this, Is it being used by the
hackers from years ago?
Reports online inform that, this bug has been fixed by the Apple, but not informed anyone about this.
If you are a website owner and using Linux servers, so always go for a routine check for any updates for your operating system.
If there is any crack or update related to this comes out, we will
update this post soon, but for now, you should secure yourself, by keep
watching your security updates





